DRAG DROP -Drag and drop the elements from the left into the order for incident handling on the right.Select and Place:

Refer to the exhibit. An attacker gained initial access to the company’s network and ran an Nmap scan to advance with the lateral movement technique and to search the sensitive data. Which two elements can an attacker identify from the scan? (Choose two.)

Refer to the exhibit. Which technology produced the log?

Refer to the exhibit. An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server. Which display filters should the analyst use to filter the FTP traffic?
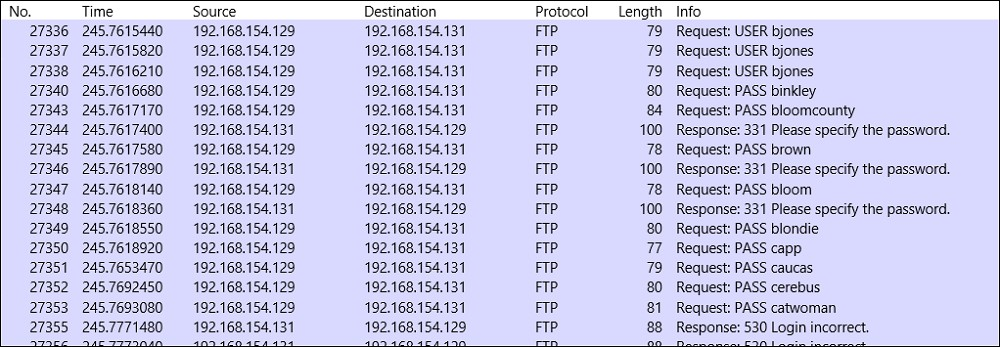
Refer to the exhibit. Which frame numbers contain a file that is extractable from Wireshark PCAP?

A cyberattacker notices a security flaw in a software that a company is using. They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software. To which category of the Cyber Kill Chain model does this event belong?
