Company A permits visiting business partners from Company B to utilize Ethernet ports available in Company A's conference rooms. This access is provided to allow partners the ability to establish VPNs back to Company B's network. The security architect for Company A wants to ensure partners from Company B are able to gain direct Internet access from available ports only, while Company A employees can gain access to the Company A internal network from those same ports. Which of the following can be employed to allow this?
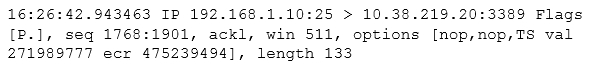
After reviewing the following packet, a cybersecurity analyst has discovered an unauthorized service is running on a company's computer.Which of the following ACLs, if implemented, will prevent further access ONLY to the unauthorized service and will not impact other services?
The new Chief Technology Officer (CTO) is seeking recommendations for network monitoring services for the local intranet. The CTO would like the capability to monitor all traffic to and from the gateway, as well as the capability to block certain content. Which of the following recommendations would meet the needs of the organization?
While a threat intelligence analyst was researching an indicator of compromise on a search engine, the web proxy generated an alert regarding the same indicator. The threat intelligence analyst states that related sites were not visited but were searched for in a search engine. Which of the following MOST likely happened in this situation?
Which of the following remediation strategies are MOST effective in reducing the risk of a network-based compromise of embedded ICS? (Choose two.)
SIMULATION -The developers recently deployed new code to three web servers. A daily automated external device scan report shows server vulnerabilities that are failing items according to PCI DSS.If the vulnerability is not valid, the analyst must take the proper steps to get the scan clean.If the vulnerability is valid, the analyst must remediate the finding.After reviewing the information provided in the network diagram, select the STEP 2 tab to complete the simulation by selecting the correct Validation Result andRemediation Action for each server listed using the drop-down options.Instructions -STEP 1: Review the information provided in the network diagram.STEP 2: Given the scenario, determine which remediation action is required to address the vulnerability.If at any time you would like to bring back the initial state of the simulation, please select the Reset All button.






