Which two statements about the FortiAnalyzer Fabric topology are true? (Choose two.)
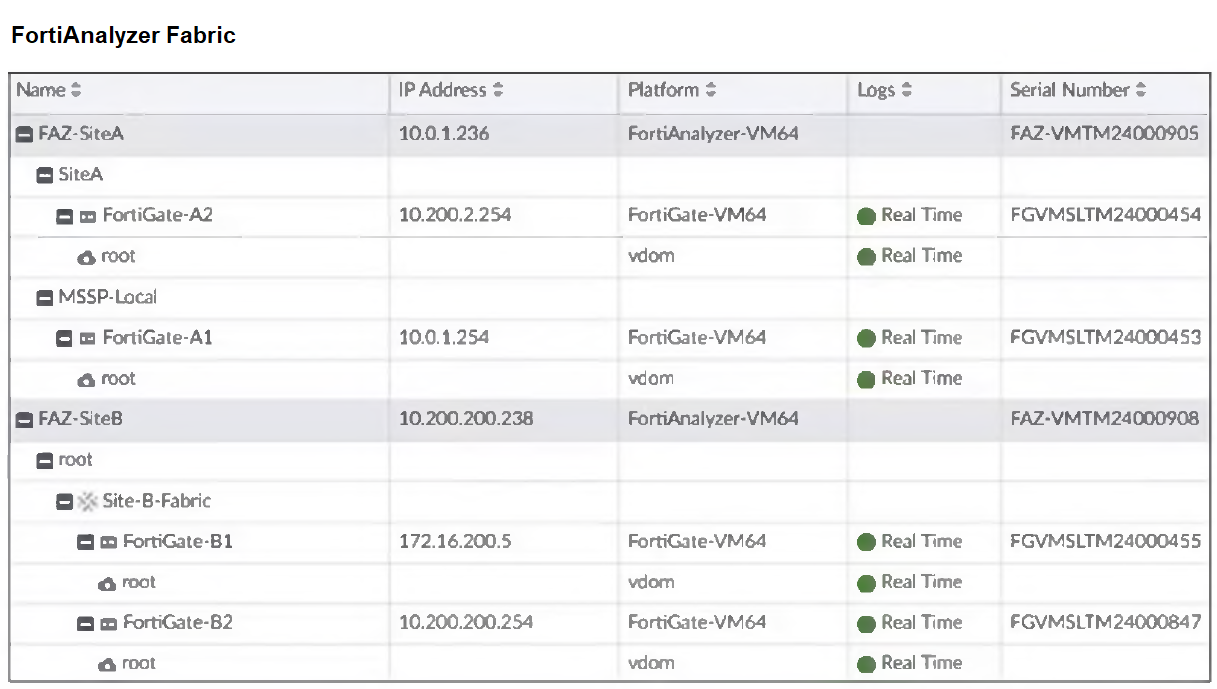
Refer to the exhibit.Assume that all devices in the FortiAnalyzer Fabric are shown in the image.Which two statements about the FortiAnalyzer Fabric deployment are true? (Choose two.)



Which three end user logs does FortiAnalyzer use to identify possible IOC compromised hosts? (Choose three.)
