Several users in your Microsoft 365 subscription report that they received an email message without the attachment.You need to review the attachments that were removed from the messages.Which two tools can you use? Each correct answer presents a complete solution.NOTE: Each correct selection is worth one point.
You have a hybrid Microsoft 365 deployment that contains the Windows 10 devices shown in the following table.You assign a Microsoft Endpoint Manager disk encryption policy that automatically and silently enables BitLocker Drive Encryption (BitLocker) on all the devices.Which devices will have BitLocker enabled?

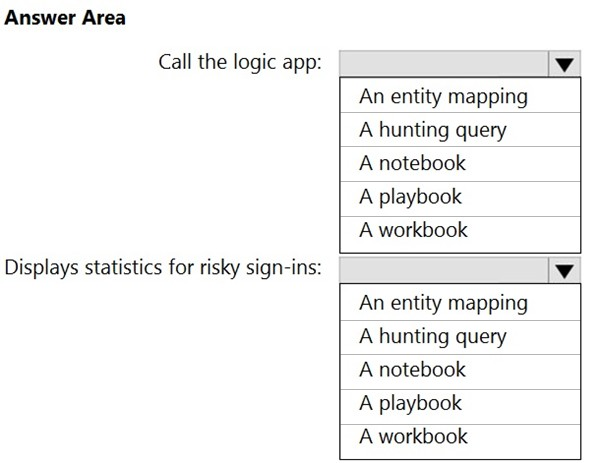
HOTSPOT -You have an Azure Sentinel workspace.You configure a rule to generate Azure Sentinel alerts when Azure Active Directory (Azure AD) Identity Protection detects risky sign-ins. You develop an AzureLogic Apps solution to contact users and verify whether reported risky sign-ins are legitimate.You need to configure the workspace to meet the following requirements:✑ Call the Azure logic app when an alert is triggered for a risky sign-in.✑ To the Azure Sentinel portal, add a custom dashboard that displays statistics for risky sign-ins that are detected and resolved.What should you configure in Azure Sentinel to meet each requirement? To answer, select the appropriate options in the answer area.NOTE: Each correct selection is worth one point.Hot Area:
DRAG DROP -You have an Azure subscription and a Microsoft 365 subscription.You need to perform the following actions:✑ Deploy Microsoft Sentinel.✑ Collect the Office 365 activity log by using Microsoft Sentinel.Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.Select and Place:

You have a Microsoft 365 subscription that contains several Windows 10 devices. The devices are managed by using Microsoft Endpoint Manager.You need to enable Microsoft Defender Exploit Guard (Microsoft Defender EG) on the devices.Which type of device configuration profile should you use?
You have several Conditional Access policies that block noncompliant devices from connecting to services.You need to identify which devices are blocked by which policies.What should you use?
